How to Enhance Network Security with EIGRP MD5 Authentication
Introduction
Authentication is an essential factor for digital devices. If we connect the devices to the internet, then authentication becomes necessary. Authentication plays a vital role in data transmission. Without encryption and authentication, there is a risk of data alteration. By default, EIGRP uses no authentication between its routers. EIGRP uses MD5 and SHA-256 authentications. However, EIGRP MD5 authentication is the most widely used. Most of the EIGRP-speaking routers use the MD5 cryptographic algorithm for their authentication. It uses the hash function to create a unique signature for each routing update. The signature is referred to as a message digest.
EIGRP MD5 Configuration
1) Define the key chain:
First, we have to define the key chain. A key chain will be given a name.
2) Assign Key Number:
The next phase is to assign a numerical identifier, or key number, that ranges from 1 to 2147483647.
3) Define the shared key:
At the end, append a shared key to the key-string command. All the routers that use the same key must have the same shared key.
4) Connect the key chain to the interface:
It is incomplete without appending the key chain configuration to the interface. Navigate to the interface mode and specify the addition of the EIGRP and its A.S. number to the keychain name. Finally, we will define the mode of authentication, MD5, in our case.
Lab Topology for MD5 Authentication in EIGRP
In our EIGRP MD5 authentication lab, we will use three routers: R1, R2, and R3. Assign the routers an IP address as shown in the topology diagram.
Similarly, configure EIGRP on all routers with autonomous system number 1. Run the show IP route on all routers for convergence. Moreover, ping each interface to check connectivity issues.

First, we check the neighbors’ table of Each EIGRP’s routers, i.e., R1 and R2.

Also, check R2’s neighbor table.
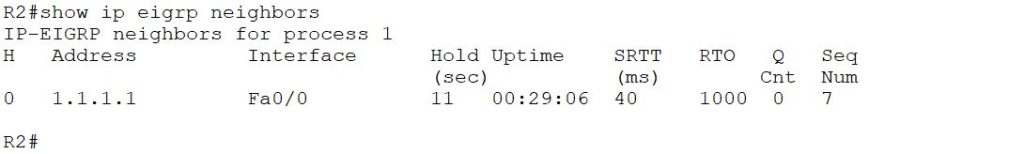
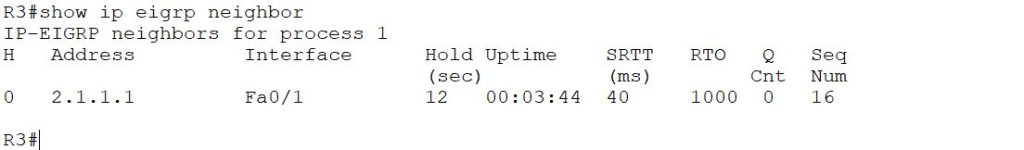
Finally, check the R3’s neighbor table.
When we enable authentication on R1, R1 will break its relationship with R2. After allowing the same authentication on R2, R2 will make R1 its neighbor again, and now R2 will break its ties with R3 because there is no authentication on R3.
R1 authentication configuration
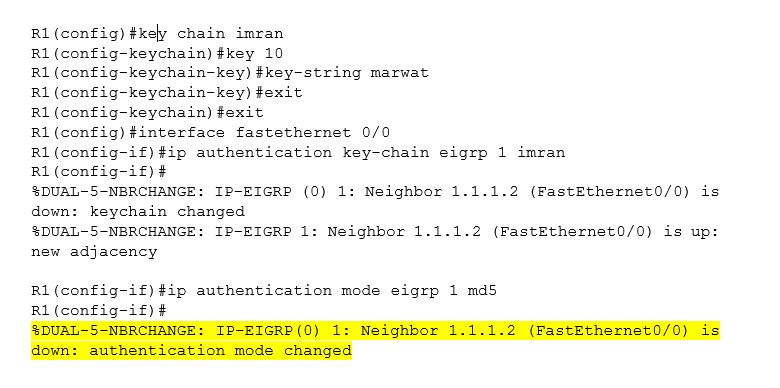
The highlighted color line indicates that R1 has been disconnected from R2 due to authentication. R2 does not have authentication, so R2 is not R1’s neighbor.
R1#show ip eigrp neighbors.
IP-EIGRP neighbors for process 1
Now, the same authentication process must be configured on R2 to enable authentication on R2.
Configure MD5 authentication for R2.
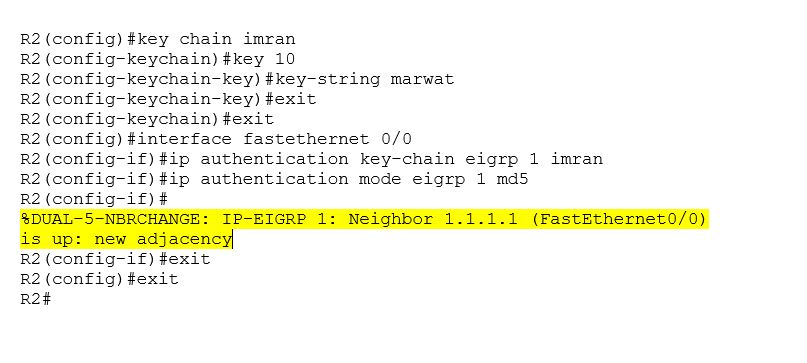
The highlighted line in the configuration showed that R2 has been reestablished in a relationship with R1.
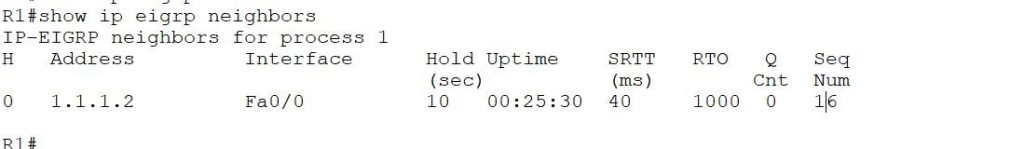
Let’s check the neighbor table on R1 and R2
R1
While the neighbor table on R2
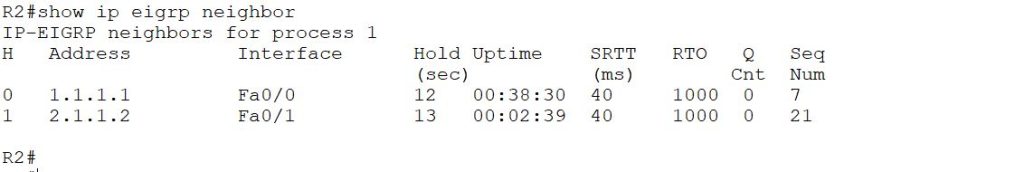
We have enabled authentication on R2, but it is still in a relationship with R3. Why? We enabled authentication only on Fastethernet 0/0 and not on Fastethernet 0/1, which is why R2 is still a neighbor of R3. If we enable authentication on the FastEthernet interface 0/1, R2 will disconnect from its neighbor ship with R3.
Now authentication on R2 interface FastEthernet 0/1
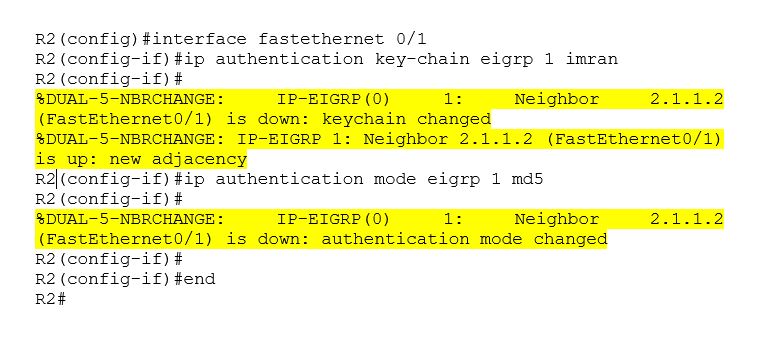
From the highlighted part of the configuration, it is clear that it has down its neighbor ship with R3 as
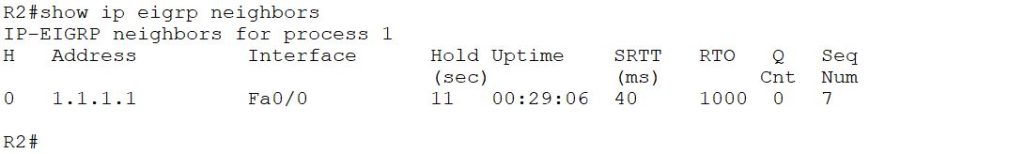
It is only a neighbor of R1. To make neighbor R2 with R3, we will configure the same authentication on R3
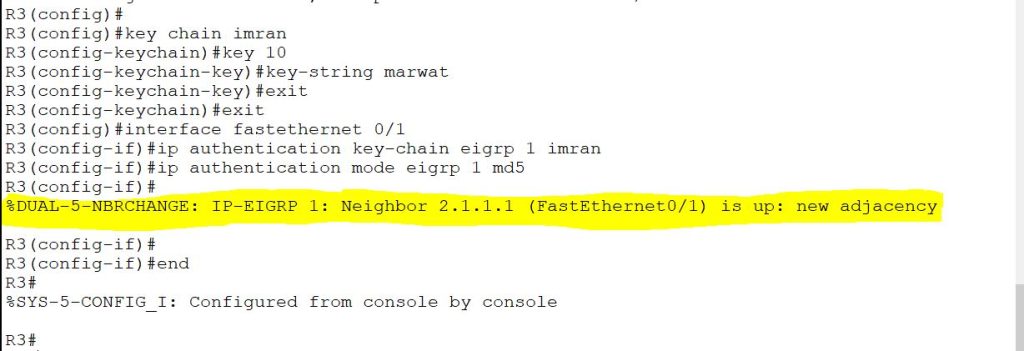
The router R3 shows that it has now made its adjacency with R2.
First, check the neighbor table of R2.

Before we configured R3’s authentication, the neighbor table of R2 had only one entry, 2.1.1.2. However, when we configured R3’s authentication, there was another entry, 2.1.1.2, in the neighbor table of R2.
Now check the neighbor table of R3

At last, we will ping R3’s FastEthernet 0/1 interface to check connectivity. If R1 is able to ping 192.168.3.1, then we will know that the topology is working and there is no issue with it.
Let’s try