How to Enable Dynamic ARP Inspection to Improve Network Defense
What Is Dynamic ARP Inspection (DAI)?
There are many ways through which an attacker can enter into network, causing network failure or stealing confidential information. ARP spoofing is one of the methods, just like DHCP spoofing. As we have learned, DHCP snooping works against DHCP spoofing. In the same way, Dynamic ARP Inspection works against ARP spoofing. ARP spoofing is an attack that is used as a man-in-the-middle attack, which responds to the ARP requests. DAI works as a firewall against ARP spoofing to stop this type of attack. DAI uses an IP-to-MAC binding table, which decides which interface is trusted and which is not!
Understanding ARP Spoofing Attacks
ARP spoofing is an attack that responds to the ARP requests. The attacker binds the legitimate user’s MAC address to his IP address. After binding IP to MAC, He shares this binding with other PCs through the Gratuitous ARP. After Gratuitous ARP, all the other PCs update their tables, and thus all other users will send traffic to this attacker instead of legitimate users.
How to configure DHCP snooping?
First of all, activate the DHCP snooping feature on the switch by using the following commands. Also, specify the vlan you are using in your network environment.
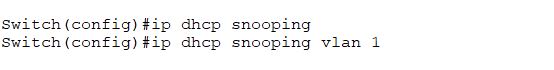
As we have a DHCP server in our lab, so we will configure the trust port for this interface as a legitimate DHCP server in case of DHCP spoofing.

After configuring DHCP snooping in the global configuration mode, the next step is to configure DAI!
How to Enable Dynamic ARP Inspection (DAI) on the Switch?
Just like DHCP snooping, enable ARP inspection in the global configuration mode on the switch.

Secondly, go to interface mode and configure those ports as trustworthy that are connected to the core devices, such as routers, firewalls, or servers.

The below command is used to prevent ARP attacks (ARP storms) that will cause the switch to be overwhelmed. So it works as rate limiting on untrusted ports.
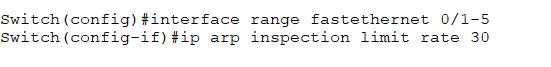
Therefore, all the above interfaces will get 30 ARP packets per second.
Difference Between ARP Spoofing and DHCP Spoofing
Both ARP spoofing and DHCP spoofing are network attacks that function as man-in-the-middle attacks. The goal of both attacks is to disrupt communication; however, their mechanisms differ, which are presented in the form of a table below
| Feature | ARP Spoofing | DHCP Spoofing |
| Protocol | Data Layer Protocol (Layer 2) | Network Layer Protocol (Layer 3) |
| Goal | DHCP spoofing installs a rogue DHCP server in the network in the presence of a legitimate DHCP server, to respond to DHCP Discovery messages | DHCP spoofing installs a rogue DHCP server in the network in the presence of a legitimate DHCP server, to respond to DHCPDiscovery messages |
| Mechanism | The attacker sends a spoofed gratuitous ARP message to falsely claim itself as the legitimate owner of a specific IP address. | Installing a rogue DHCP server on the network to respond to DHCPDISCOVER messages from clients with the attacker’s pre-configured settings. |
| Purpose | It allows the attacker to intercept traffic destined for the spoofed IP address, which can lead to denial-of-service by disrupting ARP tables. | DHCP spoofing redirects client traffic through a rogue DHCP server, leading to data theft or denial-of-service attacks. |
| Prevention | Primarily, ARP spoofing can be prevented using Dynamic ARP inspection on network switches. Moreover, port security can also provide protection. | It allows the attacker to intercept traffic destined for the spoofed IP address, which can lead to a denial-of-service by disrupting ARP tables. |