Unlocking the Secrets of Authentication Authorization and Accounting
AAA stands for Authentication Authorization and Accounting. It is a security service, which means no authorized person will not access your device or network. It is a service that stores usernames and passwords in a centralized location.
.AAA consists of three A’s, which first A is for Authentication. Authentication means who is logged in to the system or the network. A system will authenticate only this person who has the right username and password. The user will not get access to the system, having the wrong username and password. The second A is for authorization, which means which person is allowed into the system. What task can the person perform to whom we have given access to the system? While, the third stands for accounting. Accounting keeps a record of a user’s activity.
If a network has no AAA-based authentication, it is challenging for a network engineer to keep track of changes in the device. But you can track those changes through AAA.
Types of AAA authentication
There are two types of AAA-based authentication:
- Local-based AAA Authentication
- Server-based authentication
1 Local-based AAA Authentication
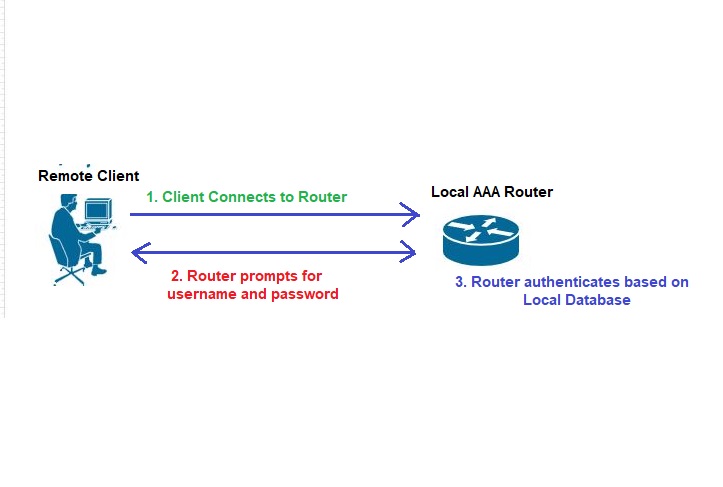
The small network uses local AAA authentication. Normally, we configure local AAA (authentication authorization and accounting) on the router or switch. We configure AAA separately on the router or switch. There is a need for a username and password in AAA authentication. So, we create a username and password in AAA. Suppose a user wants to take control of a router or switch through telnet, then it just prompts for a vty password. But, when we configure AAA on that router, then it will prompt for vty as well as for username and password. So, the router or switch will check in its database, whether it is a legitimate user or not.
The configuration for local authentication in the Cisco router is as below:
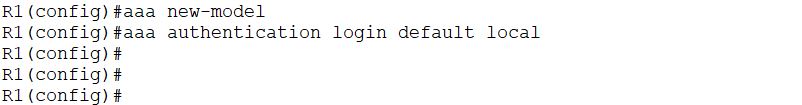
The first command enables the AAA model, while the second states that uses the local method, where the router will check locally the configured username and password.
As the AAA uses a username and password, so create any user on the router:
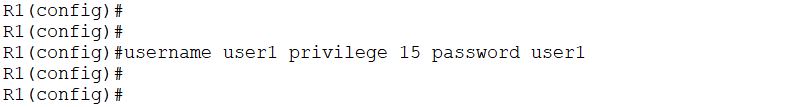
Create a local user in the router, with privilege level 15, and the user password is also user1. Also, configuration of a vty lines:
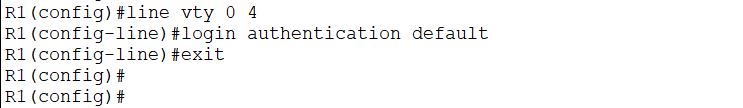
The ‘default’ represents, we will use the specific authentication method on the specified lines.
Server-Based AAA authentication
This model is suited for enterprise networks. If the enterprise network has multiple routers, switches, firewalls,s and other networking devices, then we can use such a model, e.g. Cisco ACS, or Cisco ISE. If you don’t want to store your username and password locally on a router, but in a centralized location. Normally, an enterprise network adopts AAA server-based authentication.
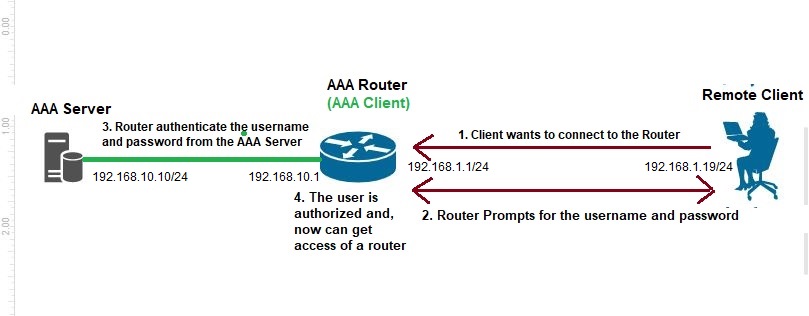
The client wants to establish a connection with the router. The router prompts for the username and password. When the client enters the username and password, then the router authenticates the entered username and password from the AAA server. When the username and password of a user match with the AAA server’s username and password, then the router gets access to the user.
Configuration of AAA server authentication

The communication protocol between the client and AAA server will be, whether tacacs+ or radius. Tacacas+ stands for terminal access controller access-control system plus. While radius stands for remote access dial-in user services.
The key differences between Tacacs+ and radius server
| Tacacs+ | Radius | |
| Standard | Cisco Propriority | Open standard |
| Transport Protocol | TCP based using port no. 49 | Uses two ports UDP port no. 1812 and 1813 |
| Confidentiality | It encrypts the entire packet | Only password is encrypted |
| Authorization | It supports authorization | There is no explicit command for authorization |
| Accounting | It does support accounting | It also supports accounting |
| Functionality | Tacacs+ separate authentication and authorization traffic | It also supports accounting |