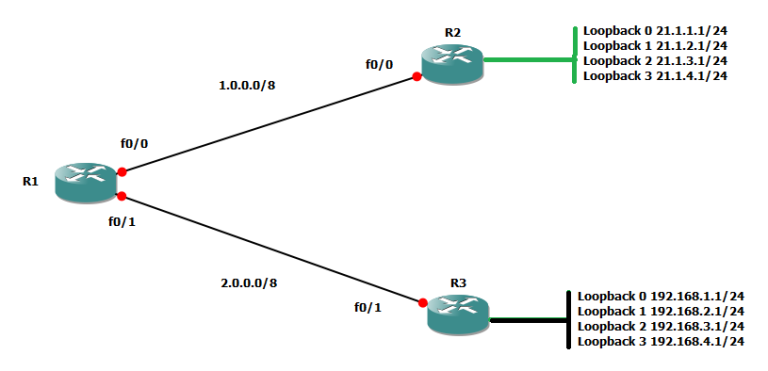
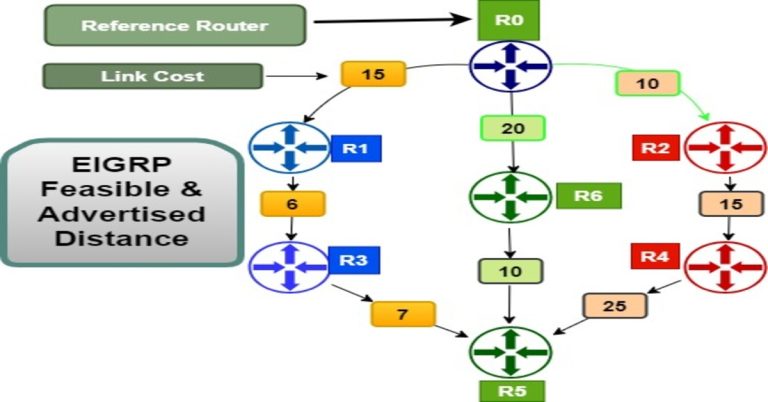
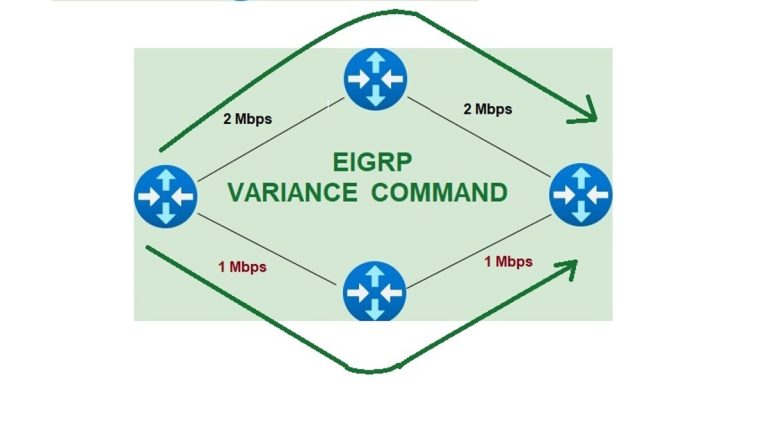
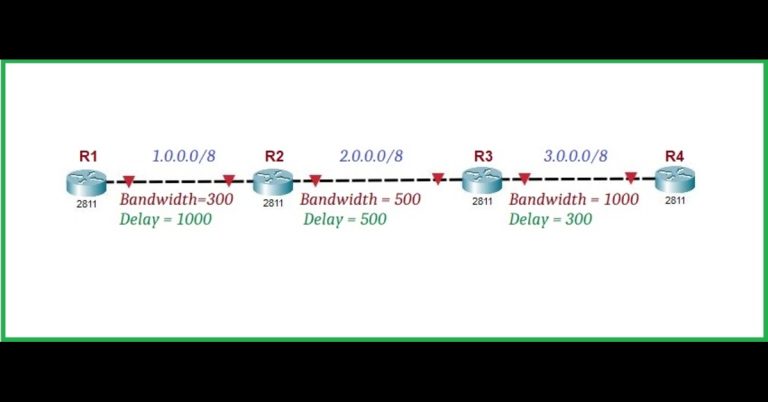
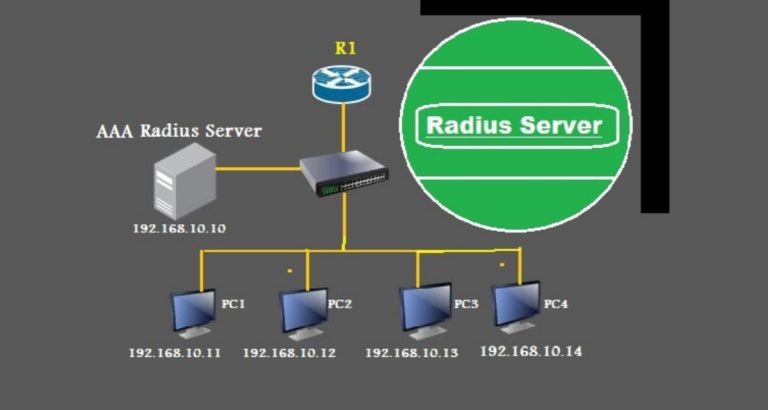
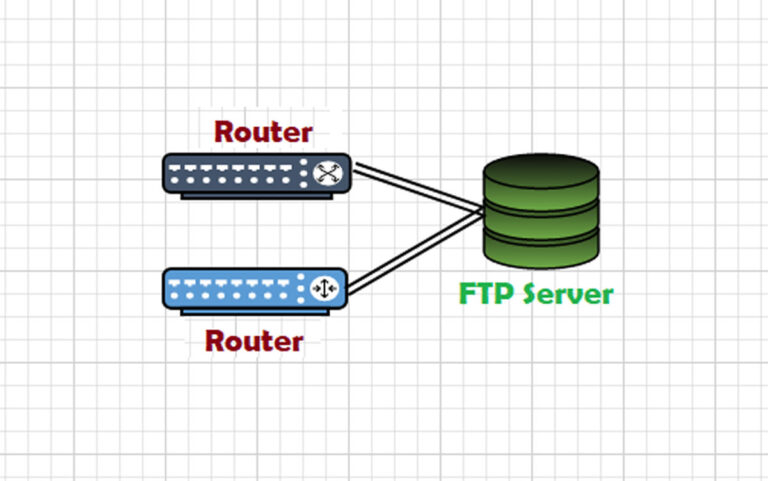
How to Set Up 802.1X Authentication in Cisco Packet Tracer
In today’s enterprise network environments, the implementation of NAC (Network Access Control) is no longer optional, but it is mandatory. One of the most robust and widely used protocols for port-based network access control is IEEE 802.1X. 802.1X is a framework through which we implement authentication at Layer 2. It acts as a guard that…